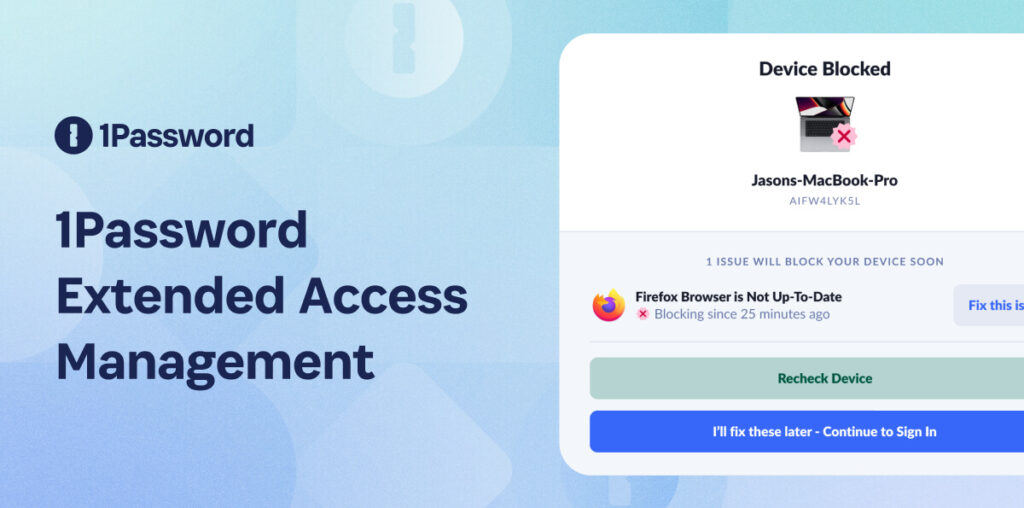
Today’s security tools only secure access to some applications, some devices, and some people. With remote work, bring-your-own device, and shadow IT apps becoming commonplace, the number of unsanctioned apps and untrusted devices is rapidly climbing. Businesses are stuck relying on traditional identity and access management solutions, which were built for a way of work that no longer exists.