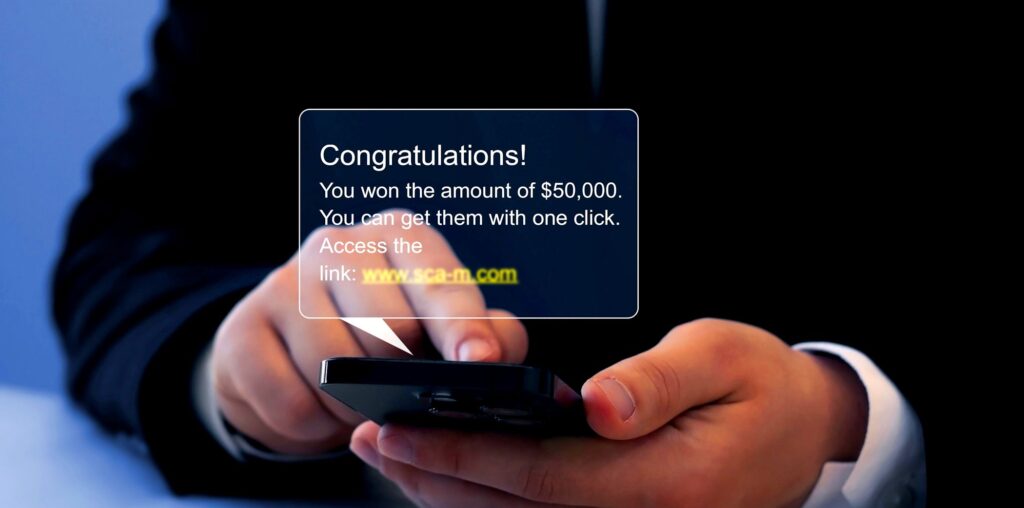
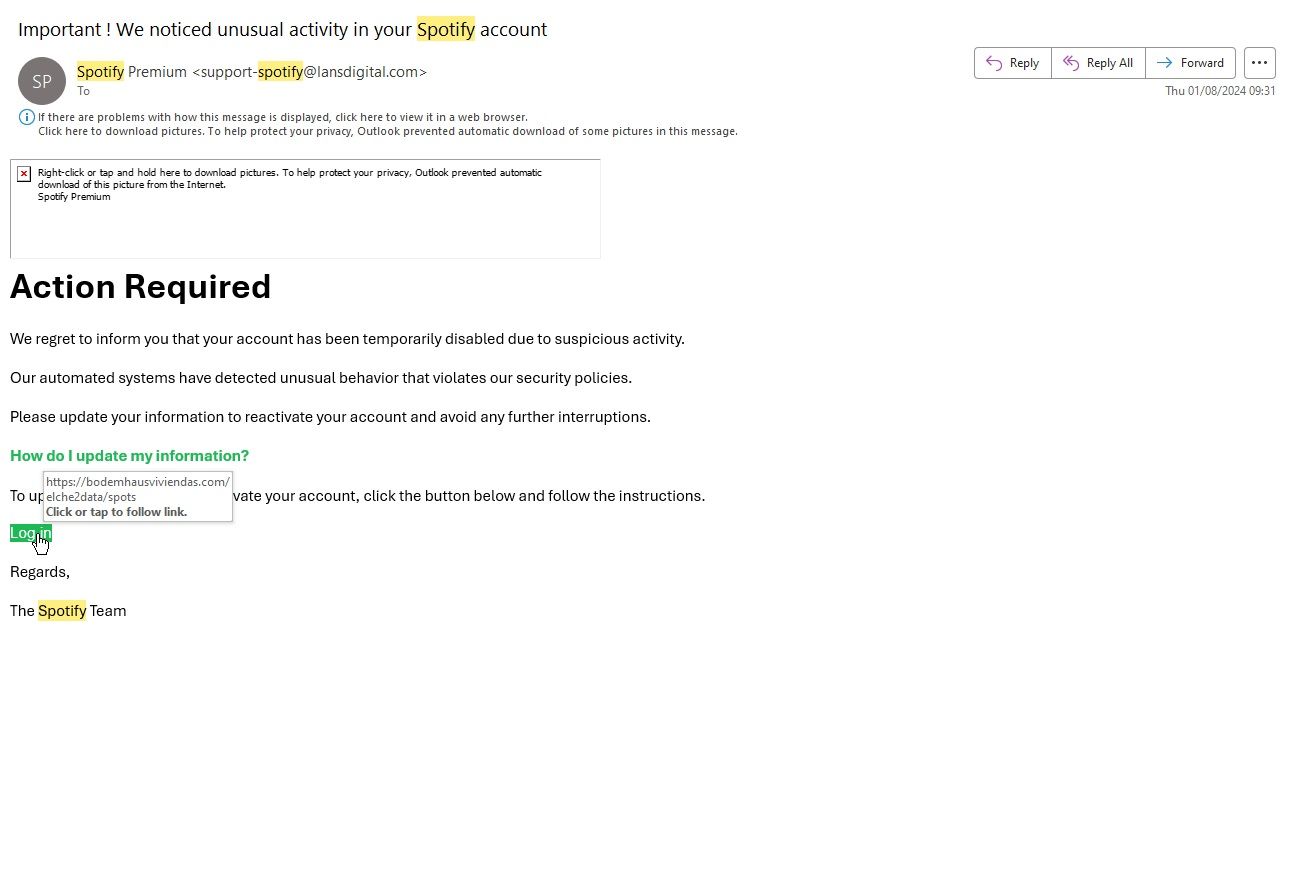
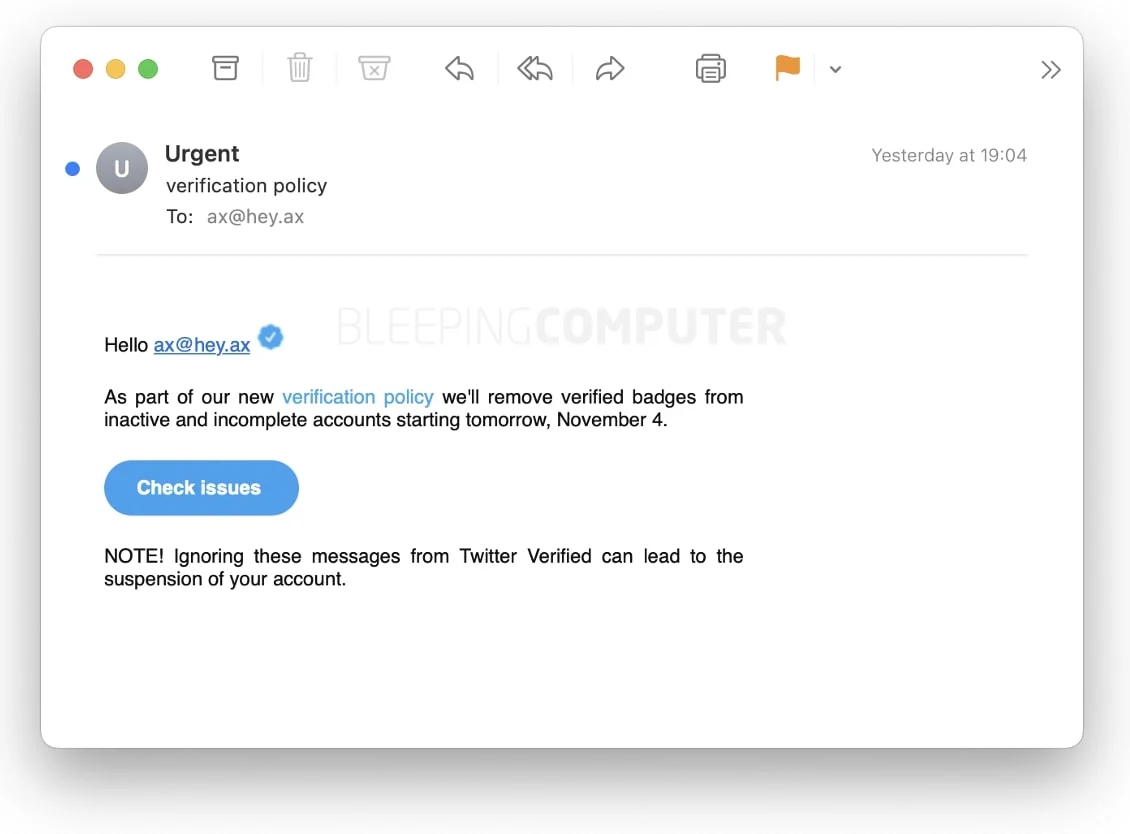
The FBI estimates that Americans lost a whopping $12.5 billion to phishing schemes in 2023. You might think you can identify a fraudulent email and avoid becoming a statistic; however, a malicious email is just one of the many phishing attacks cybercriminals use.
Email Phishing
Originally, a phishing attack only referred to an attempt to steal sensitive information or money via email. That’s because email was one of the first attack vectors criminals used to scam people online. It is still one of the most popular phishing schemes, with an estimated 3.4 billion emails sent daily, and is the FBI’s most reported crime.
The vast majority of phishing emails used to be easy to identify. Poor grammar and odd word choice were dead giveaways that the email was fake. That has changed since the rise of generative AI like ChatGPT, which helps hackers with no knowledge of English quickly craft emails that can con anyone.
If you’re wondering if an email is real, contact the alleged company directly, not by responding to the email. And whatever you do, if you’re unsure if an email is authentic, don’t click any links or download any attachments.
Smishing
Most people check a text within five minutes of receiving it because texts, unlike emails, are usually sent by friends, family, and companies we trust.
Smishing is the same as email phishing, except instead of receiving a fraudulent email, you receive an SMS. You’ve likely received a text from Amazon alerting you of a package arrival despite not placing an order. Or maybe you received a text from a stranger who claims to have the wrong number but still insists on starting a conversation with you. Both are instances of a criminal attempting to have you click on malware or to dupe you into giving them money.
Pig butchering is an increasingly popular smishing attack in which an attacker gains your trust before convincing you to invest in something (typically a fake crypto exchange) and ultimately steals your investment.
Angler Phishing
We post a wealth of information on social media for all to see. Scammers will use this information to create a highly personalized angler phishing attack.
An attacker combs through your social media to learn about the products and services you use. They then pose as a customer service representative from a company they’ve ascertained you use. They’ll ask for sensitive details, send a malicious link, or link to a fake website to steal your password or other details they can use to access your account.
Vishing
Recently, a confident and cordial person claiming to be from Wells Fargo phoned me to say a suspicious payment had been made with my card and that they needed to verify my identity. The first thing they asked for was my social security number.
This vishing attack had every key ingredient a social engineering attack needs to succeed. They said that time was of the essence, scared me into almost giving them sensitive information, and pretended to have the authority to ask for this information from me.
Thankfully, scam-blocking features and apps can reduce malicious calls, but you should still be wary.
Spear Phishing
As mentioned, billions of phishing emails are sent daily. Most of these are the same emails sent out in bulk, pretending to come from a legitimate business, but they are not personalized.
Spear phishing is a much more personalized attack. Imagine if an email you received used your name and contained sensitive information. Naturally, you’d be much more inclined to open it.
Spear phishing attacks aren’t used on the average person; rather, they are reserved for someone the hacker deems to be of high value. A hacker might invest time and money into gathering details about their target to construct a highly personalized malicious email.
One variant of the spear phishing attack is “whaling,” which is used for even higher-value targets, such as C-suite executives and CEOs.
Watering Hole
A watering hole attack works by compromising a legitimate website. Attackers can take over an entire website or find a vulnerability and inject HTML or JavaScript code that redirects users to a spoofed website. As users trust this website, they are more likely to openly click on links and provide information such as credit card information, social security numbers, and login credentials.
Website Spoofing
Have you ever tried going to Amazon.com but accidentally typed Amazonn.com? Despite arriving at a website that might look and feel exactly like Amazon, it’s actually an impersonator website owned and operated by fraudsters. In a process known as typosquatting, criminals purchase domain names similar to popular websites. They make these websites look similar, except they are wholly designed to collect your sensitive information.
While phishing attacks are getting more difficult to spot, you can keep yourself safe by refraining from clicking on links or providing sensitive information until you have verified beyond all doubt that the person you’re corresponding with is from the company in question.